API Setup
Service Architecture
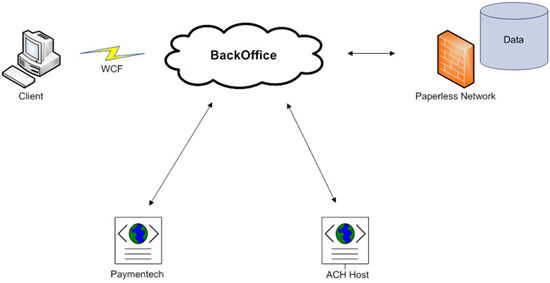
How to Communicate
For sake of this documentation, the term service will be used to refer to API. The term consumer will be used to refer the party consuming the functionality of the service.
Consumers will interact with the service by sending and receiving SOAP transmissions. The BackOffice service is transport protocol independent, and is able to communicate with consumers on any platform, over any protocol. These protocols include (but are not limited to) HTTP and TCP/IP.
The service is associated with a unique internet address. The consumer must provide the location of the service, as well as the transport schema that will be used.
| Protocol | Address |
|---|---|
| HTTPS | https://svc.paperlesstrans.com:9999/?wsdl |
| TCP/IP | net.tcp://svc.paperlesstrans.com:8002/BackOffice |
Security
The transmission of credit card and bank account information requires a solid defense. In order to protect the financial assets of your constituents, the following safeguards have been put in place.
- Encrypted Key: Each terminal will be required to provide a key uniquely associated with the MID. This key will be hashed during transmission. A connection will not be established until the terminal has authenticated with a valid key.
- Permissions: All terminal functions will be permission based. Requests that do not meet permission rule set for the calling terminal will be denied.
- IP Restrictions: All connections validated using the IP address from which the terminal/consumer is calling. Terminals whose IP address does not match the IP on file will not be able to connect.
- WSDL Security: The "Web Service Security Policy" uses a mechanism within the WSDL's metadata to publish identity information. Consumers using the WSDL are to be provided the identity information ahead of time. When consumers connect to the WSDL the published identity information will be matched to the prerecorded identity information.
- SSL Transmission: All WSDL communications must be transferred over a SSL/TLS/HTTPS (X509 certificate) connection. The X509 certification on both the consumer and server will allow for mutual authentication. X509 certificates use an encryption key size of 1024 bits or higher.
- Authentication Reversion: Once a consumer has completed its connection with the WSDL the connection will revert to a fully unauthenticated state. This will also occur if the two sides are unsuccessful at establishing a complete connection. There would be no ability to "continue" a connection.
